Here is my first blog post of 2025. Have a great year!
Sample Details:
SHA256 Hash: 7899ea0aa36bacb8d2f94907373e550cec71d02701107cb2ef3cf629c305f877
Package Name: com.errorforcode.netix
Application Name: بسته معیشت
Analysis
Starting with AndroidManifest.xml, the app has a launcher activity MainActivity, has a Firebase Messaging Service and Receiver, a broadcast receiver to listen for incoming SMS Messages and a service.
Looking into MainActivity
- Whole lot of string decryption takes places by reading the values stored in core.txt, acc.txt and ns.txt present in
assetsfolder. - The entire decryption process is present in this script
- In short, this app loads the url
https[:]//irna.space/itsOK/app/in a webview. Here is how the website looks like (taken from Wayback Machine)

- Also it requests for permission related to SMS, Contacts and Phone calls.
- Whole lot of string decryption takes places by reading the values stored in core.txt, acc.txt and ns.txt present in
Broadcast Receiver :
GetSMS- works as a receiver for incoming SMS messages
- collects the message content and address of the sender
- sends the incoming intent to start the service
SMSService
Service :
SMSService- checks message content to execute commands sent by the attcker
- ping : device sends a feedback mssg to attacker to notify it is working
- hide : hide the app from the menu
- unhide : unhide the app from menu
- last : collects the last message of the device
- chrome , change : both commands change the icon of the application
- normal : turns the icon back to normal mode
- checks message content to execute commands sent by the attcker
This app also has a Firebase Cloud Messaging Service and Receiver that acts as a listener for the attacker to send commands to the device.
Receiver
- intent filter with action :
com.google.android.c2dm.intent.RECEIVE - works when the Cloud FCM sends a message to the device
- working is similar to C2 Architecture
- each message contains : action , chat_id and androidid
- intent filter with action :
Attacker Commands (defined in Customized FCM Service)
send2contact : attacker will send the text to send, in SendToContact there is a function
getContactList
that returns list of all phone numbers , both of these information to passed through a series of functions
where finally the text is sent usingsmsManager.sendTextMessage()unhideone : unhide the app icon on the menu
allsms : Attacker will specify how many sms should be collected. based on that, the app will collect that many mssgs provided by the
content providercontent://sms. once concatenated , it will be encrypted and sent back to the servermashatautotar : Spam messages to the contacts every n seconds
get_clipboard : Gets the text present in the clipboard
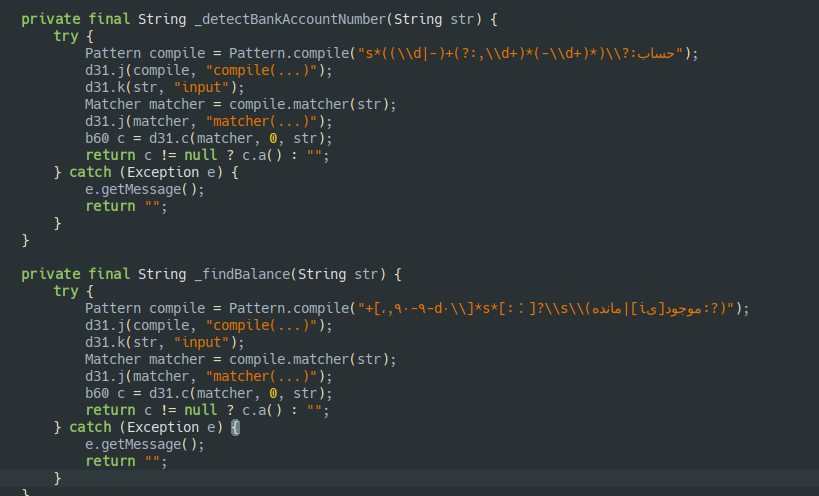
getbalance
- Iterates every message present in the device
- detects the bank name (they check for Iran based banks like KESHAVARZI, IZBANK , Bank Mellat)
- detect balance from the message (seems iranian banks formats it in weird regex)
- detects account numbers from the body of message (only pattern i could recognize where
\\d{3}-\\d{3}-\\d{7}-\\d) - Sends bankname, sender address , balance , date and acc number to the server
screenshot: takes screenshot of the device , sends it in encrypted base64 format
set_clipboard: using setPrimaryClip function of ClipboardManager, it sets the text provided by the attacker as the primary clip
updateport and updatesudo : updates the text present in port.txt and sudo.txt respectively with attacker data
lastsms : sends information regarding the last sms in the device
updateaddress : updates the domain address of the attacker server
ussd :
- USSD code is provided by the attacker
- Sends a request using TelephonyManager.sendUssdRequest(), and when the response is successful (due to onReceiveUssdResponse handler) , it sends USSD response to the attacker
contactnumbers and allcontact
- Collect name and phone number from the list of contacts , encrypt the data and send it to the server
cardnumbers
- Gets all SMS and checks the content of the message body with a extensive regex that checks for pattern that starts with 4 digit number
followed by 12 digits
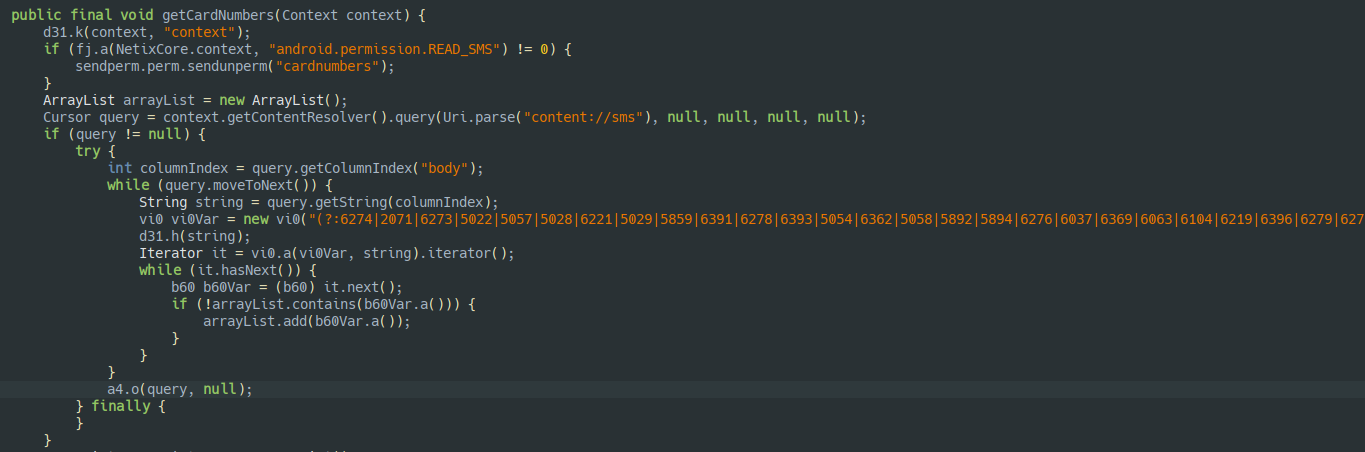
- The messages that passes this check are passed to a function to collect the bank info based on the card number
- Gets all SMS and checks the content of the message body with a extensive regex that checks for pattern that starts with 4 digit number
fullinfo
- Collects info whether the app has read sms , receive sms , send sms , read contacts , and notification permissions and send all these
info to the server
- Collects info whether the app has read sms , receive sms , send sms , read contacts , and notification permissions and send all these
allsaderats
- Specifically for messages from Bank Saderat Iran
- Tries to collect account number and balance from the message sent by the above bank (has a different regex pattern)
getphone: Collects the phone numbers available and checks if the phone code is based of Iran (+98)
Conclusion
This was an intersting sample to analyze. This was also the first time seeing Messages and Cloud FCM functionality to send attacker commands. I had a lot of fun analyzing this sample.
GG’s <3